In today’s dynamic digital world, cyber threats are becoming increasingly complex and pervasive. One of the most serious threats are keyloggers, which can intercept sensitive data typed by users. To counter these threats, VMware Horizon has introduced an advanced keylogger blocking feature. This innovative technology helps organizations safeguard against unauthorized access to data by effectively detecting and blocking keystroke interception attempts. As a result, the security level of virtual work environments is significantly raised, which is crucial for protecting sensitive corporate information.
What does this look like in practice?
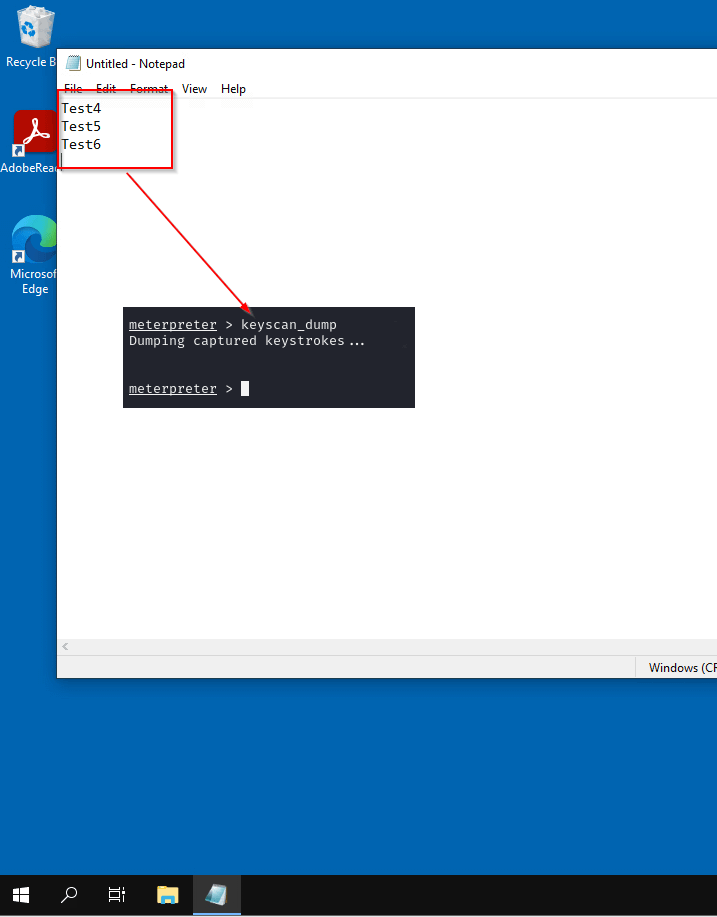
A user infected with malware typing whatever characters in whatever application transmits everything to the attacker. For example, a user types something in Notepad, for example, as in the following screenshot:
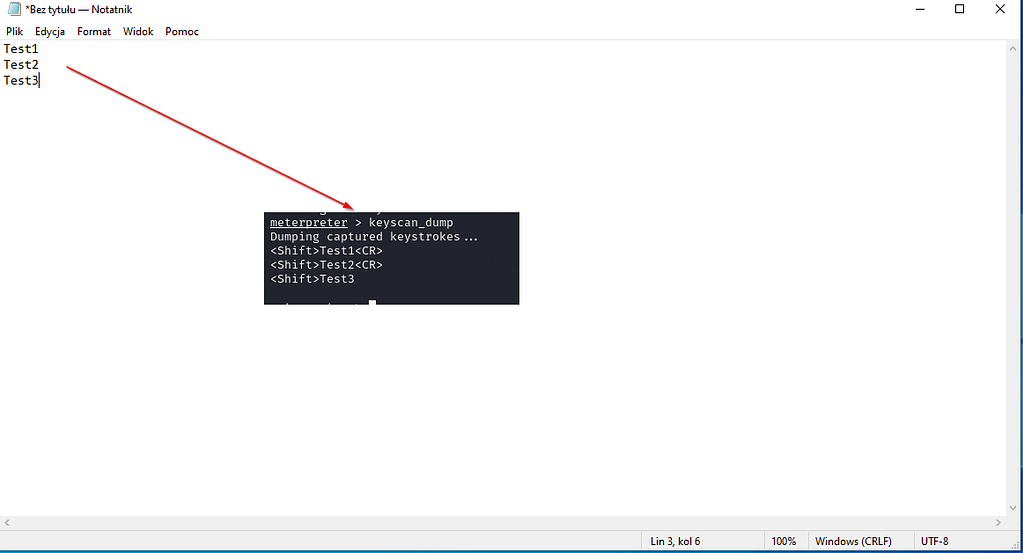
The user typed a sequence of characters in notepad:
- <Shift> – indicates indentation of the shift key, as shown by the first capital letter,
- Test1 – typed text,
- <CR> – pressing the enter button.
So as you can see, the text is passed 1:1, even including keys such as shift, enter, ctrl, etc.
Vmware Horizon offers protection against such software, so that even having a keylogger on the station, an attacker will not read what the user has entered.
Configuring the Keylogger Blocking service in Vmware Horizon
On a Windows client station, install the Vmware Horizon client with the Keylogger Blocking option, in manual mode, select Customize Installation after launching the installer.

In the next step, select Enable Keylogger Blocking and choose Agree & Install.
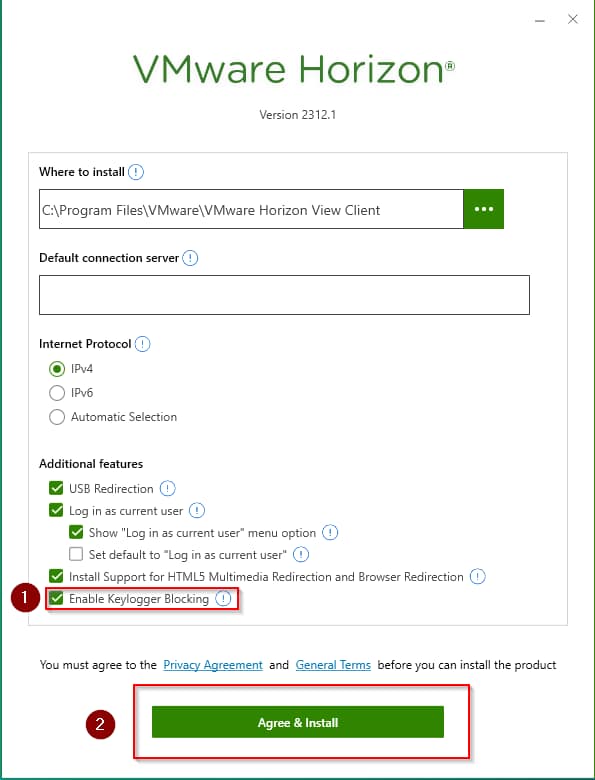
After installation, restart the system.
Alternatively, you can perform a silent installation using the command:
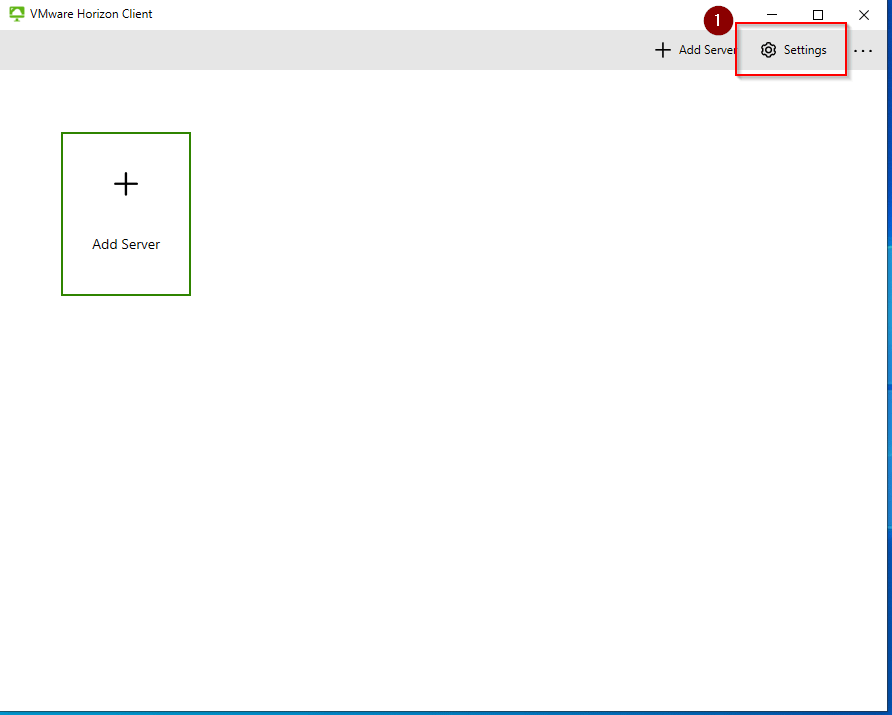
VMware-Horizon-Client-YYMM-y.y.y-xxxxxx.exe /silent /norestart KEYLOGGER_BLOCKING_ENABLED=1After launching the client, go to Settings
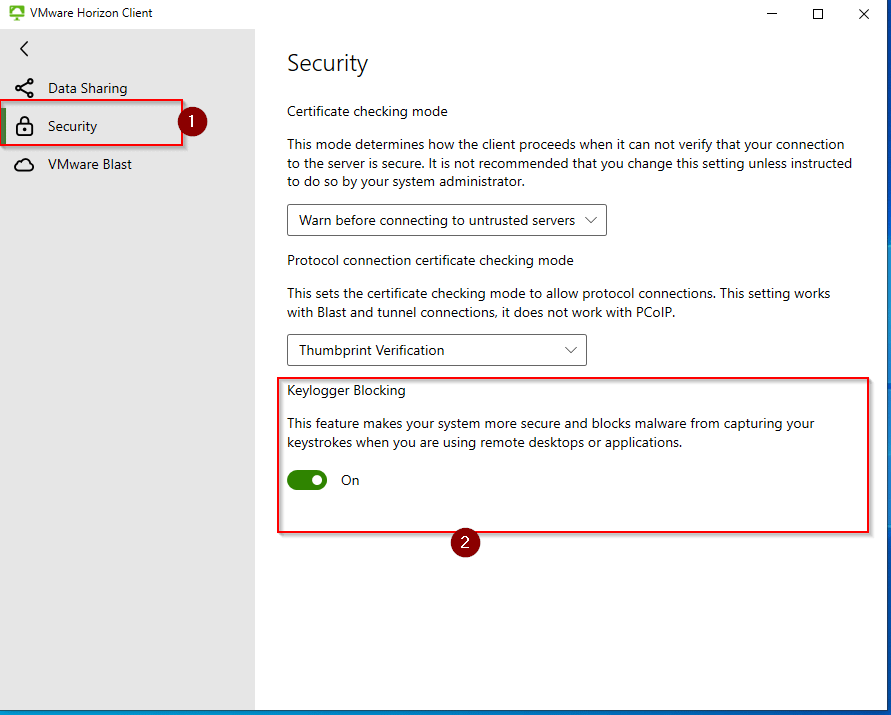
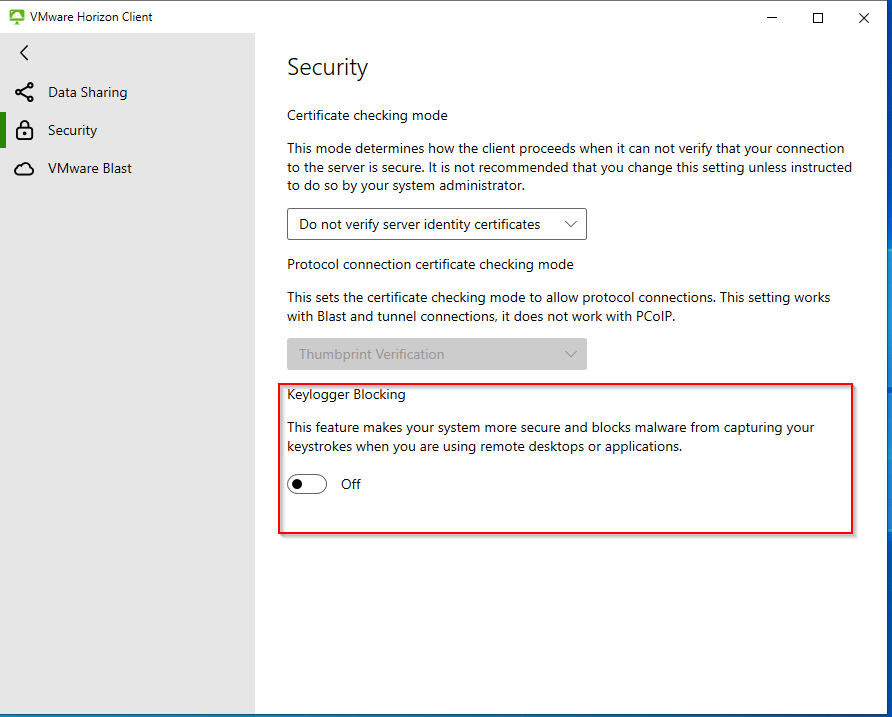
In the settings window that opens, go to Security and verify that Keylogger Blocking is set to ON
To verify, you can still run cmd and use the sc query vmwprotect command to check if the service is running.
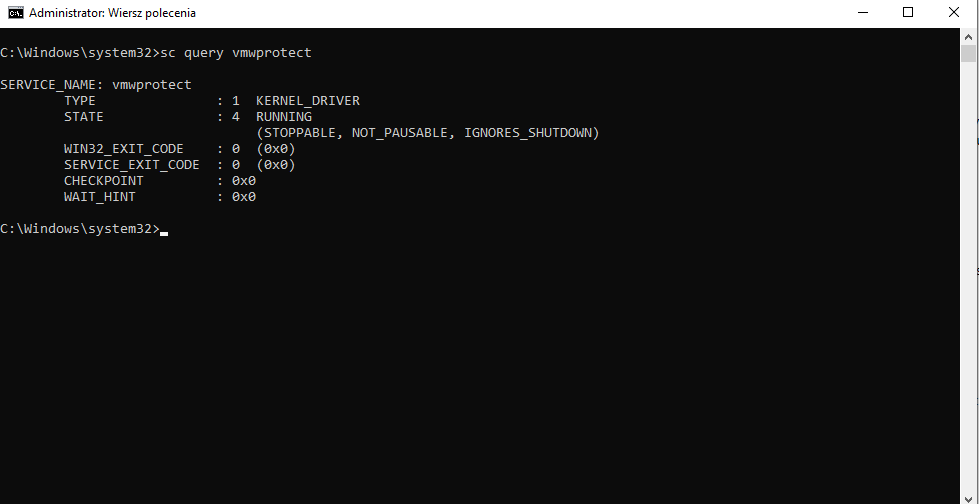
The VDI machine or RDSH server with the agent installed also needs to be configured, the best solution is to create a GPO policy under the OU where the machines are located. Details on ADMX for Horizon environment can be found at https://docs.omnissa.com/pl-PL/bundle/Horizon-Remote-Desktop-FeaturesV2312/page/ViewAgentConfigurationADMXTemplateSettings.html
In the Computer Configuration > Policies > Administrative Templates > VMware View Agent Configuration > Key Logger Blocking branch, select Enable.
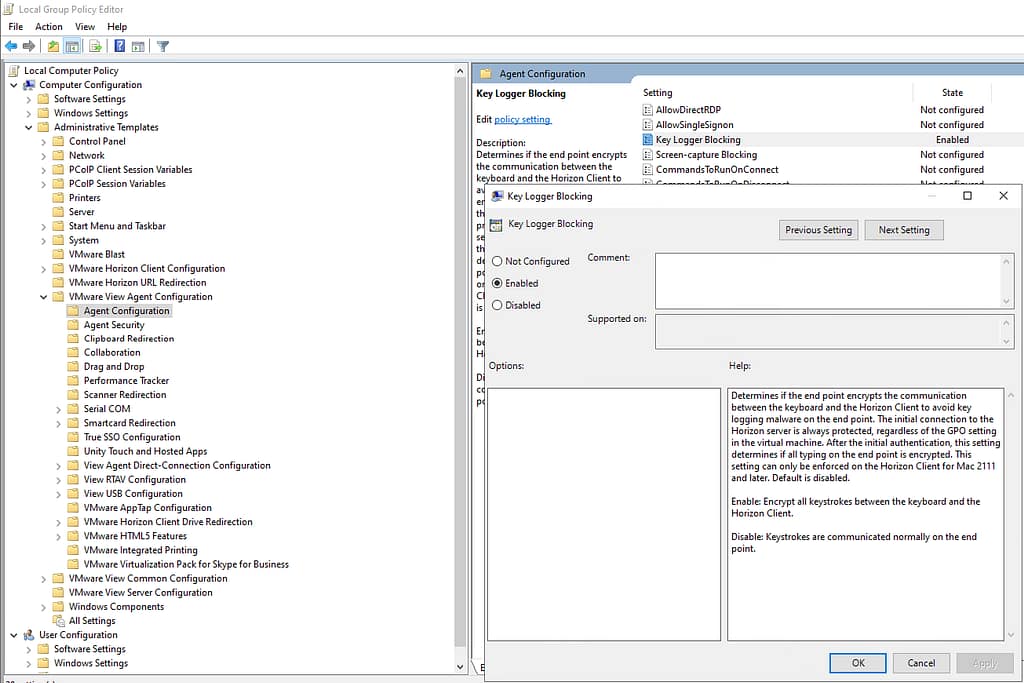
After the above configuration, the environment is now ready to defend against malware.
Now it’s time for the test!
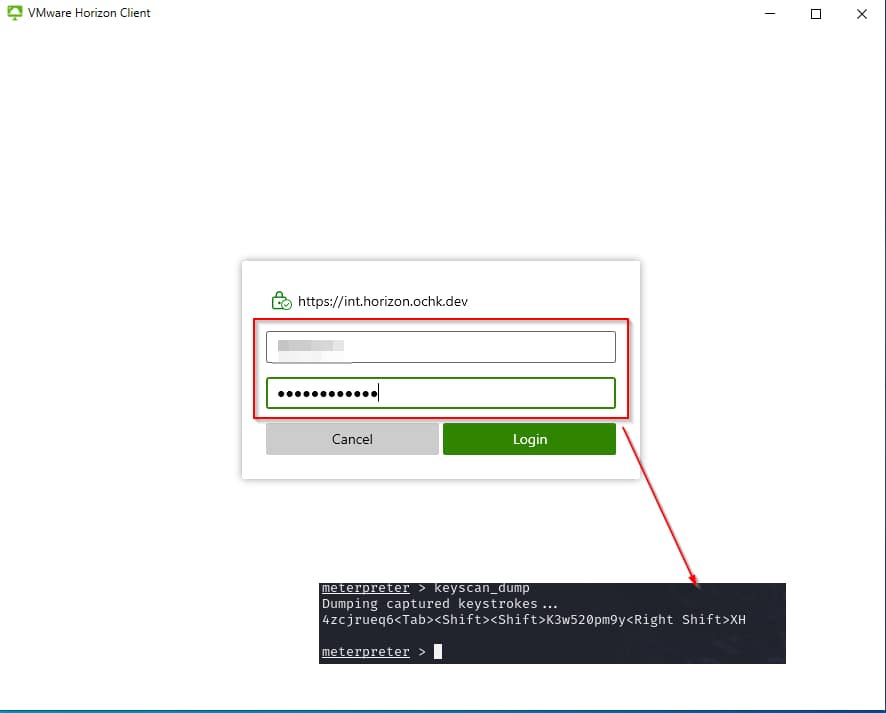
The first step domain password, so that the user can connect to his resources.
The user typed in his data and the attacker can only see a string of random characters
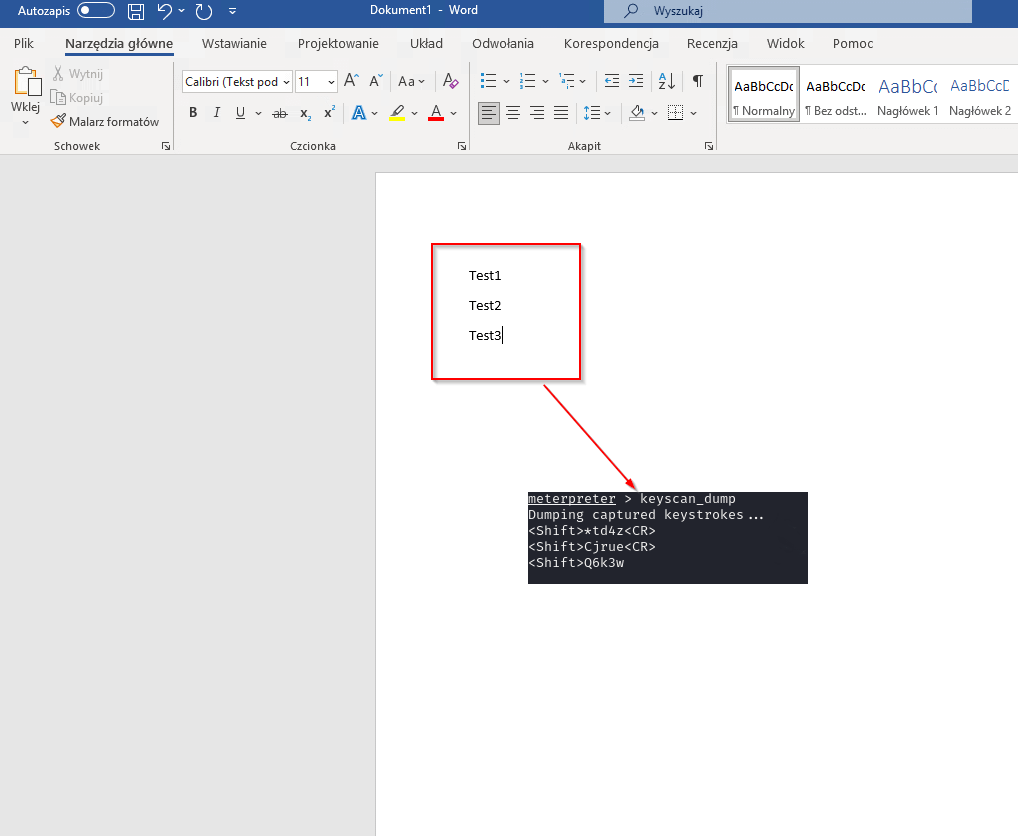
The user launched a remote Word application, typed some text, and the attacker again saw a string of characters.
If the user runs his VDI and types some text, the attacker will see a blank field on his side:
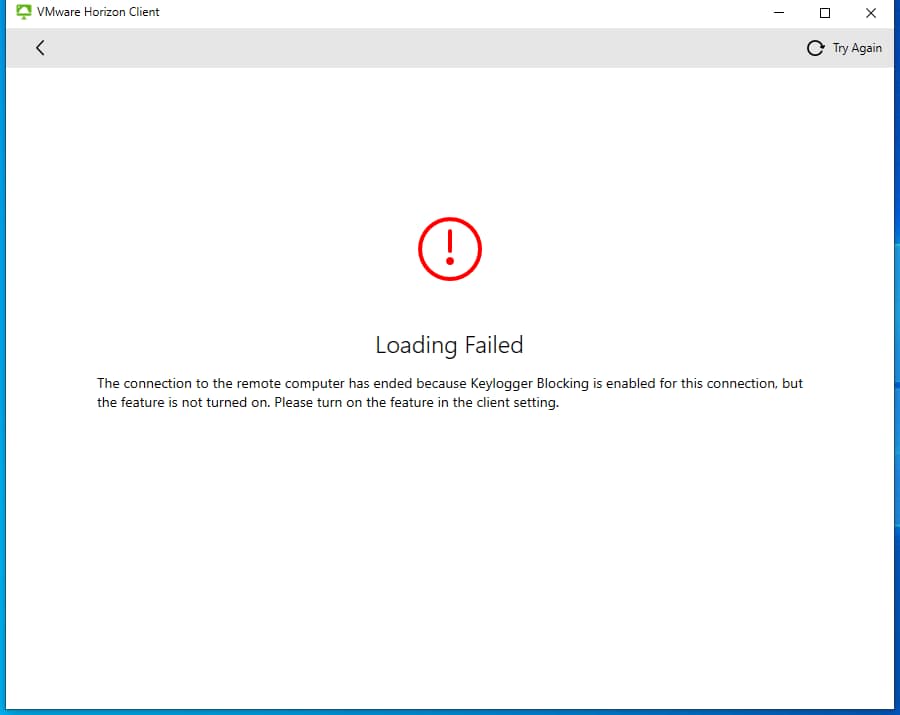
One more interesting and important thing, of course the attacker can be clever and disable the vmwprotect service, what then?
The user logging in and entering the password coprada will reveal it to the attacker, but when urchoming the application he will receive a message that he can’t run the application because Keylogger Blocking is disabled, so the user will know that there is something wrong and will take action according to the procedure in the Organization.
Summary
In the article, I described the growing cyber threats associated with keyloggers, which pose a serious risk to user data security. In response to these challenges, VMware Horizon has introduced an advanced keylogger blocking feature. This innovative technology effectively secures virtual work environments from unauthorized access to sensitive information, which not only protects typed data, but also detects and responds to attackers’ attempts to disable the service. With this solution, organizations can significantly increase the level of protection of their sensitive data.

